Network transport refers to the methods and protocols used to transfer data from one device to another over a network.
Think of it as the postal service for the internet, ensuring your data packets (like letters) reach their destination safely and securely.
Importance of Network Transport
Network transport is vital for maintaining the security and integrity of data as it travels across the internet. Here’s why:
- Data Integrity: Ensures that data is not altered during transmission.
- Data Confidentiality: Protects data from being accessed by unauthorized users.
- Data Availability: Ensures that data is available when needed, preventing disruptions.
Key Protocols in Network Transport
There are two main protocols used in network transport:
- TCP (Transmission Control Protocol)
- UDP (User Datagram Protocol)
TCP (Transmission Control Protocol)
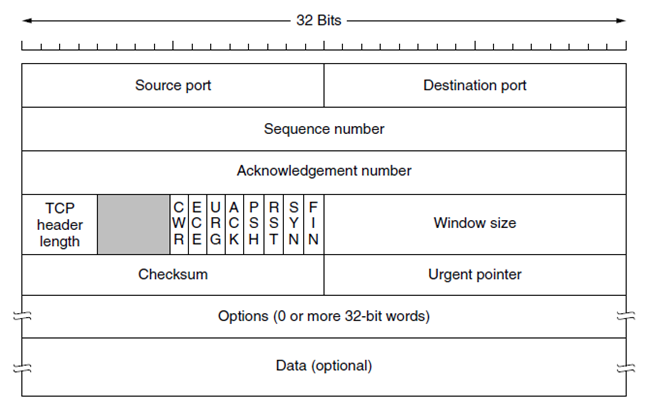
- Reliable Communication: TCP ensures that data packets are delivered in the correct order and without errors. It’s like sending a registered letter where you get a receipt confirming delivery.
- Three-Way Handshake: TCP uses the three-way handshake process to establish a connection between devices. This involves three steps:
- SYN (synchronize)
- SYN-ACK (synchronize-acknowledge)
- ACK (acknowledge).
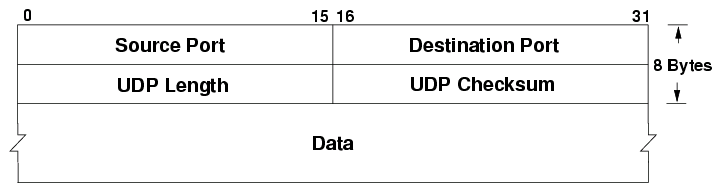
UDP (User Datagram Protocol)
- Faster but Less Reliable: Unlike TCP, UDP does not guarantee the order or integrity of data packets. It’s like sending a postcard – faster but with no delivery confirmation.
- Use Cases: UDP is often used for live broadcasts and online gaming where speed is more important than reliability.
Common Threats to Network Transport
Understanding the threats to network transport can help in data security. Some common threats include:
- Man-in-the-Middle Attacks: An attacker intercepts and possibly alters the data being transmitted.
- DDoS Attacks (Distributed Denial of Service): Overwhelms a network with traffic, making it unavailable to users.
- Packet Sniffing: Unauthorized interception and analysis of data packets.
Protecting Network Transport
- Encryption: Encrypting data ensures that even if it is intercepted, it cannot be read without the decryption key.
- Firewalls: These act as barriers between trusted and untrusted networks, blocking malicious traffic.
- Intrusion Detection Systems (IDS): These systems monitor network traffic for suspicious activity and alert administrators.
